Zowe Explorer Profiles
Zowe Explorer Profiles
After you install Zowe Explorer, you need to have a Zowe Explorer profile to use all functions of the extension. You can optionally activate the Secure Credential Store plug-in to securely store your credentials.
Working with Zowe Explorer profiles#
You must have a zosmf compatible profile before you can use Zowe Explorer. You can set up a profile to retain your credentials, host, and port name. In addition, you can create multiple profiles and use them simultaneously.
Follow these steps:
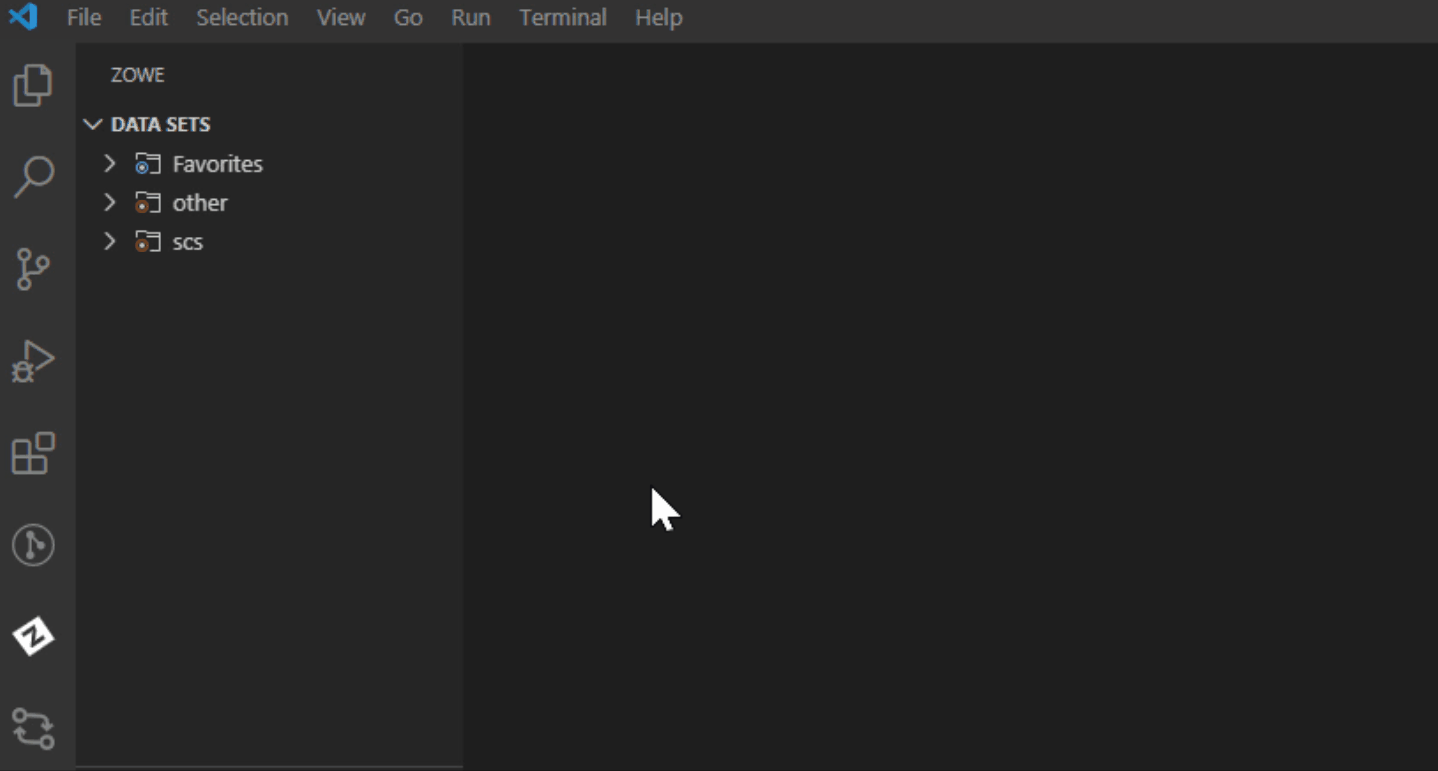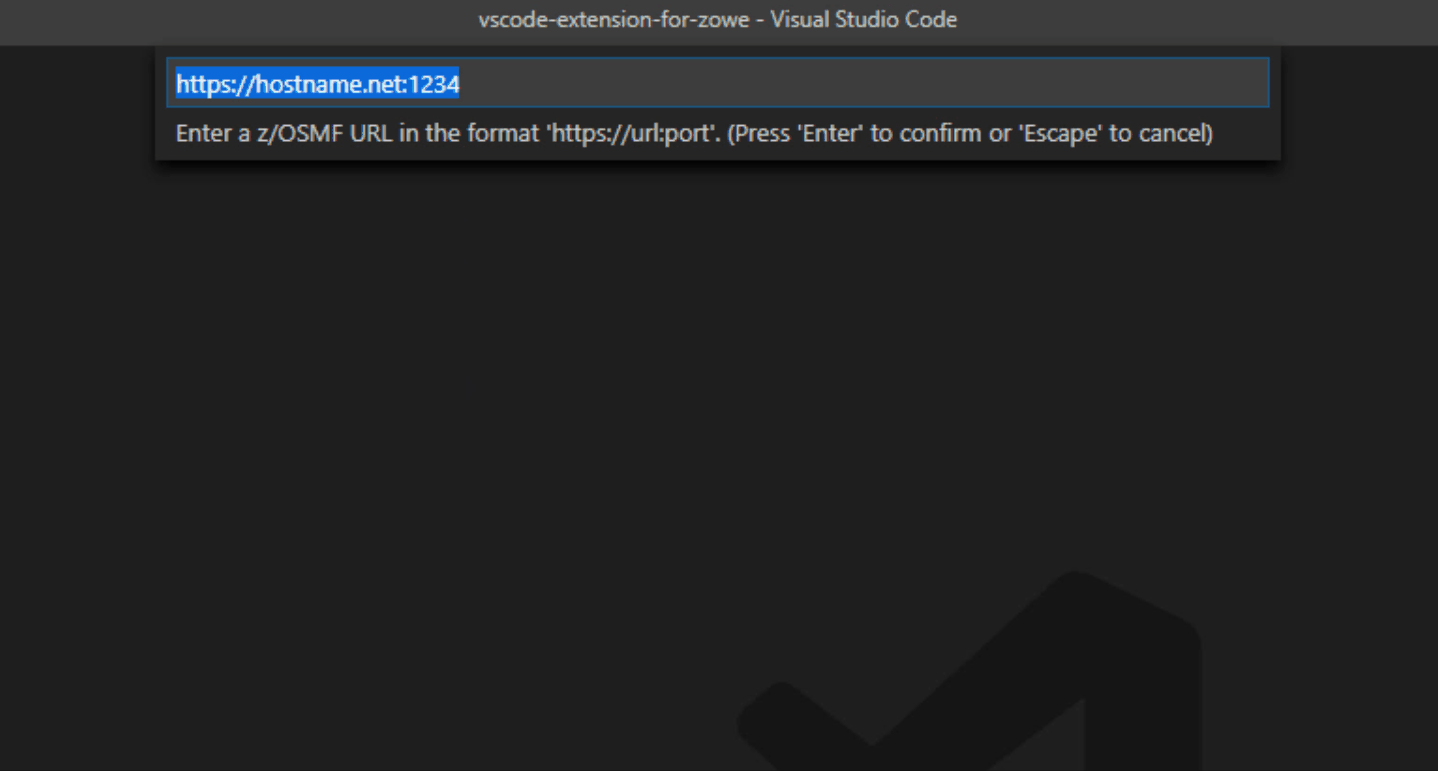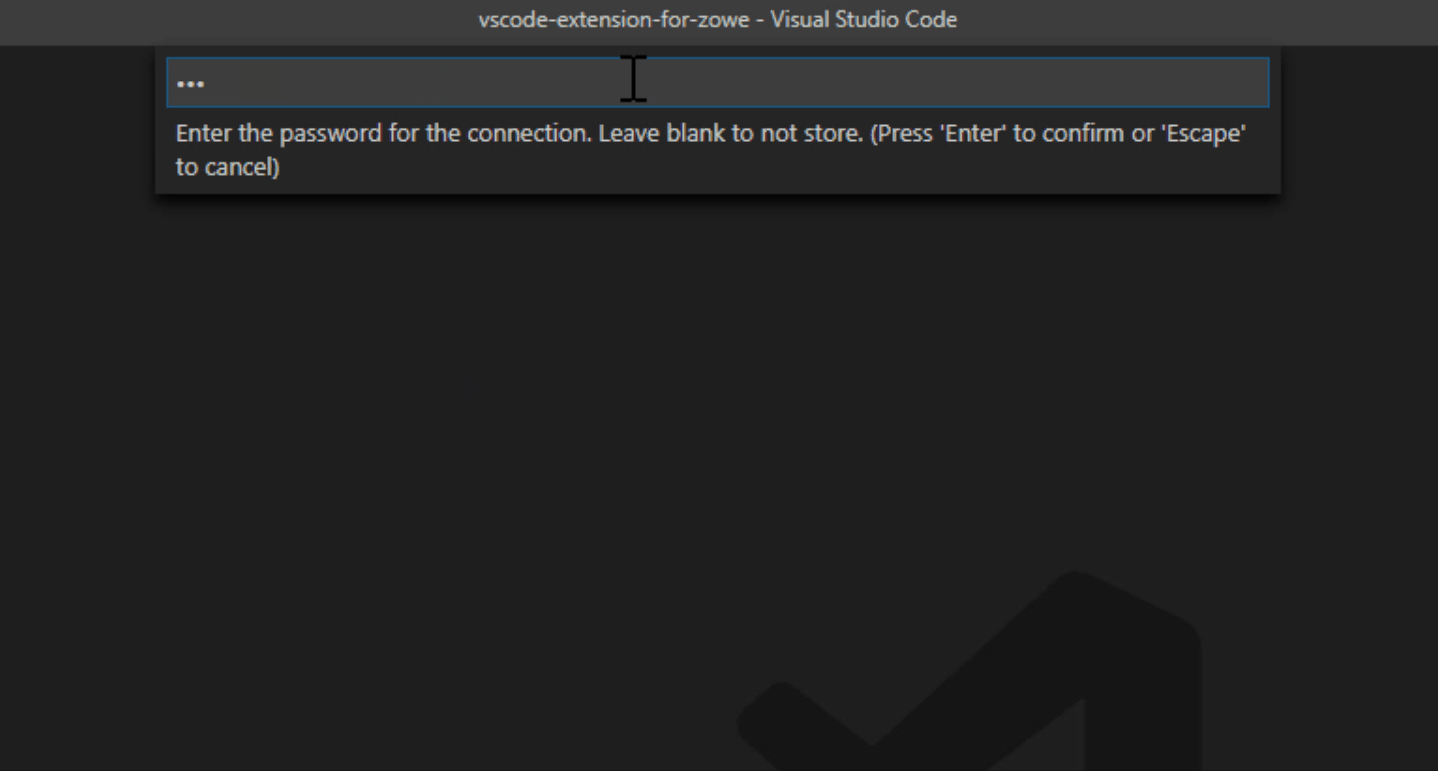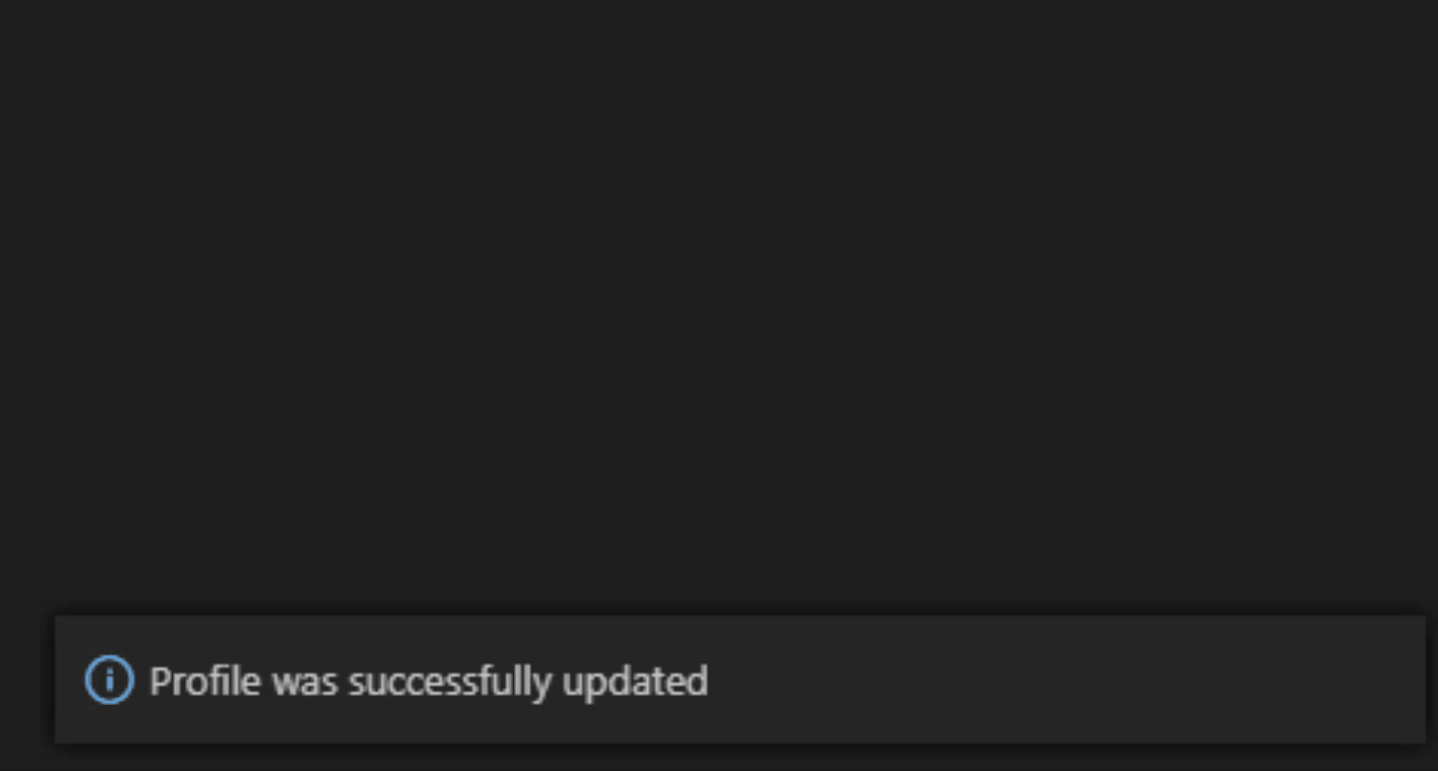
Navigate to the explorer tree.
Click the + button next to the DATA SETS, USS or JOBS bar.
Note: If you already have a profile, select it from the drop-down menu.
Select the Create a New Connection to z/OS option.
Note: When you create a new profile, user name and password fields are optional. However, the system will prompt you to specify your credentials when you use the new profile for the first time.
Follow the instructions, and enter all required information to complete the profile creation.

You successfully created a Zowe CLI zosmf profile. Now you can use all the functionalities of the extension.
If you need to edit a profile, click the Update Profile button next to the corresponding profile.
In addition, you can hide a profile from the explorer tree, and permanently delete a profile. When you delete your profile permanently, the extension erases the profile from the .zowe folder. To hide or delete a profile, right-click the profile and choose one of the respective options from the list.
Associate Profile#
Extensions built on Zowe Explorer provide users with additional functionality through unique profile types, such as RSE or FTP. The "associate profiles" function allows users to link, or associate, these extension profile types with an existing zOSMF profile. Every Zowe Explorer profile has two types of association: primary and secondary. While the primary association is zosmf, the secondary association includes Zowe CLI plug-ins or other services you might have. Within the scope of their own extender package, associated profiles can be used to access a relevant REST API that is available to the extender.
Create a secondary association for your Zowe Explorer profiles.
Follow these steps:
- Navigate to the explorer tree.
- Click the associate profiles button.
- Select a secondary profile type.
- Select a file name you want to create an association for.
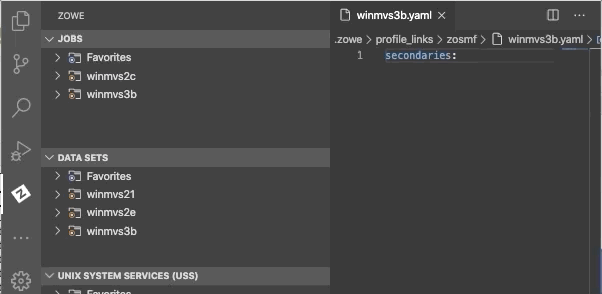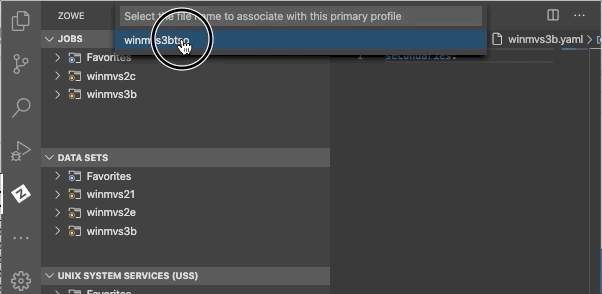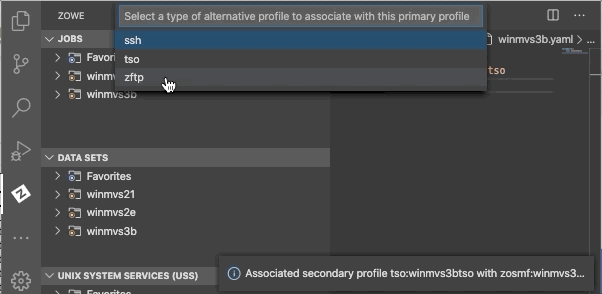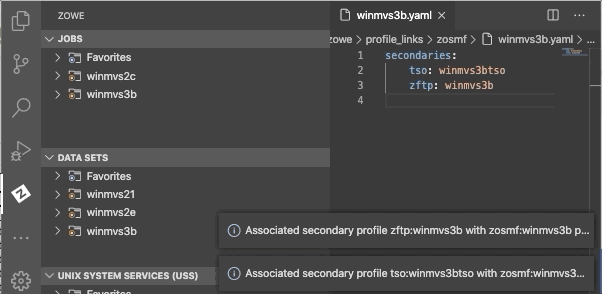
You have successfully created the secondary association for your Zowe Explorer profile.
For more information, see Associating Zowe CLI Profiles.
Enabling Secure Credential Store with Zowe Explorer#
Store your credentials securely by using the Secure Credential Store (SCS) plug-in in Zowe Explorer. By default, your credentials are stored in plain text.
Activate the SCS plug-in in Zowe Explorer.
Follow these steps:
- Open Zowe Explorer.
- Navigate to the VSCode settings.
- Open Zowe Explorer Settings.
- Add the Zowe-Plugin value to the
Zowe Security: Credential Keyentry field. - Restart VSCode.
- Create a profile.
Your Zowe Explorer credentials are now stored securely.
For Zowe CLI users#
Ensure that you install the SCS plug-in for Zowe CLI before activating SCS in Zowe Explorer. For more information about the SCS plug-in for Zowe CLI, see Secure Credential Store plug-in for Zowe Explorer.
Important: If you did not install the SCS plug-in for Zowe CLI and try to activate SCS in the extension, you will not be able to use your existing profiles, and will have to recreate them.
Activate the SCS plug-in in Zowe Explorer.
Open Zowe CLI and issue the following command:
zowe scs uOpen Zowe Explorer.
Navigate to the VSCode settings.
Open Zowe Explorer Settings.
Add the Zowe-Plugin value to the
Zowe Security: Credential Keyentry field.Restart VSCode.
The credentials of your newly created or existing profiles are now stored securely.
Use Base Profile and Token with Existing Profiles#
As a Zowe user, you can leverage the base profile functionality to access multiple services through Single Sign-on. Base profiles enable you to authenticate via Zowe API Mediation Layer. You can use base profiles with more than one service profile. For more information, see Base Profiles.
Before you log in and connect your service profile, ensure that you have Zowe CLI v6.16 or higher installed.
Access services through API ML with SSO#
Connect your service profile with a base profile and token.
Follow these steps:
Open Zowe CLI and run the following command:
zowe auth login apiml.Follow the instructions to complete the login process.
A local base profile is created that contains your token. For more information about the process, see Token Management.
Run Zowe Explorer and click the + icon.
Select the profile you use with your base profile with the token.
The profile appears in the tree and you can now use this profile to access z/OSMF via the API Mediation Layer.
For more information, see Integrating with API Mediation Layer.
Log in to the Authentication Service#
If the token for your base profile is no longer valid, you can log in again to get a new token with the Log in to Authentication Service feature.
Notes:
- The feature is only available for base profiles.
- The feature supports only API Mediation Layer at the moment. Other extenders may use a different authentication service.
Follow these steps:
Open Zowe Explorer.
Right-click your profile.
Select the Log in to Authentication Service option.
You will be prompted to enter your username and password beforehand.
The token is stored in the default base profile .yaml file.
If you do not want to store your token, request from the server to end the session of your token. Use the Log out from Authentication Service feature to invalidate the token.
Follow these steps:
- Open Zowe Explorer.
- Right-click your profile.
- Select the Log out from Authentication Service option.
Your token has been successfully invalidated.